Ciphers are the foundation of cryptography, as they are the primary tool used in the encryption process. There are two primary types of ciphers: substitution ciphers and transposition ciphers. Substitution ciphers take the plaintext and replace each character in the plaintext with its corresponding character in the key to generate the ciphertext. Transposition ciphers take the plaintext and compare it to the key to change the positions of each character in the plaintext to generate the ciphertext. To then decrypt the ciphertext generated from the cipher, you do the same process but in reverse: take the ciphertext, compare it to the key, and then reveal the plaintext. Most ciphers that you'll come across are symmetric encryption methods, meaning that there is only one shared key used between the data sender and the data receiver. However, this means that if an attacker can get hold of the key, then they can decrypt an encrypted message using said key. There's also another threat to using ciphers known as frequency analysis. In the English alphabet, different letters occur more often than others, so by observing which letters in the ciphertext occur more often, a hacker can use frequency analysis to figure out the plaintext. While not all ciphers are vulnerable to frequency analysis, and not all messages are as vulnerable (shorter messages are stronger against frequency analysis compared to longer messages), it is still generally better to use an encryption algorithm alongside a cipher to make the encryption more secure.
The following table contains a list of differnet ciphers and their applications in cyber security:
| Cipher | Application |
|---|---|
| Caesar Cipher | A cipher in which each letter of the plaintext is replaced by a letter some fixed number of positions down the alphabet. |
| ROT 13 | A cipher that replaces a letter with the 13th letter after it in the alphabet. |
| Simple Substitution | A method of encrypting data that creates the ciphertext by replacing the characters of the plaintext with those of a predetermed key. The key is a mix of letters, nubmer, and/or symbols that make up the length of the regular alphabet. |
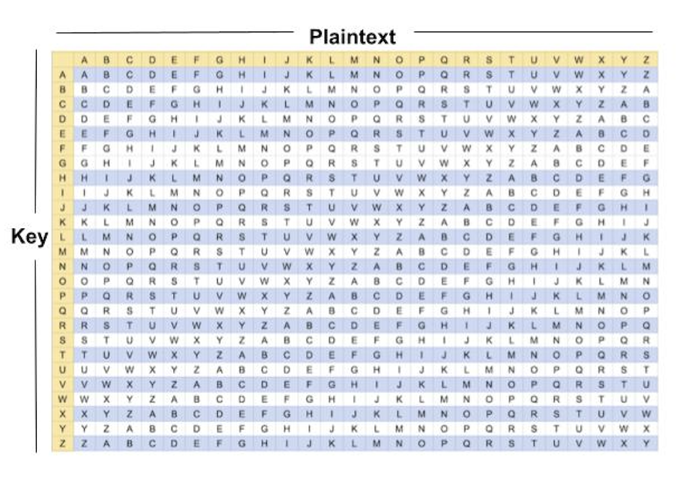
| Vigenère Cipher | A method of encrypting alphabetic text where each letter of the plaintext is replaced with a different letter on the Vigenère graph, which is determined by the letter of the plaintext and the corresponding letter of the key. |
| Transposition Cipher | A method of encryption that scrambles the positions of the characters in the plaintext without changing the characters themselves. Where each character is moved to is determined by the key. |
For more information on cryptography click here
For more information on algorithms click here
For more information on ciphers click here