Encryption algorithms are a series of steps used in the encryption process to convert plaintext into ciphertext. Most encryption algorithms will use mathematical operations in their process of converting plaintext into ciphertext by converting letters into their ASCII value. Most algorithms are also asymmetric encryption processes, meaning that they use two keys in the encryption and decryption process: a public key (that anyone can know) and a private key(that only the sender and receiver can know). There are two types of algorithms: stream ciphers and block ciphers. Stream ciphers take one character in the plaintext at a time and run it through the mathematical operations of the algorithm to generate the ciphertext. Block ciphers will take groups of characters at a time and run them through the mathematical operations of the algorithm to generate the ciphertext. Depending on which type of algorithm you use, stream or block, the system running the algorithm will require more bits of data available and more time. While stream ciphers will generally require fewer bits of data available compared to block ciphers, they will take more time to encrypt the data and are generally better for shorter messages. On the other hand, block ciphers will generally require more bits of data available but will take less time for encryption compared to stream ciphers, making them generally better for longer messages.
The following table contains a list of differerent encryption algorithms and their usage in cyber security:
| Algorithm | Useage |
|---|---|
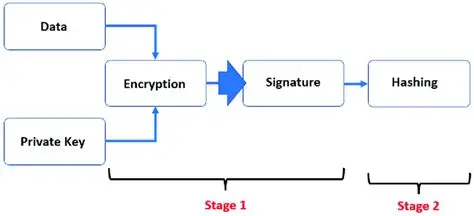
| Rivest Shamir Adleman (RSA) | Developed by Ron Rivest, Adi Shamir, and Len Adleman in 1978, this algorithm uses modular multiplication for data encryption and signature. |
| Digital Signature Algorithm (DSA) | Developed by the United States government, this algorithm can only be used for data signing and not encryption. |
| Elliptic Curve Cryptography (ECC) | Provides the same functions as RSA but for smaller devices. Where RSA is used on computers, ECC is used on smartphones. |
| Diffie-Hellman key agreement | Developed by Dr. Whitfield Diffie and Dr. Martin Hellman in 1976, the Diffie-Hellman key agreement doesn't encrypt or decrpyt data but instead generates a shared private key for the two users. |
| Hash Algorithm | Used to convert a data string into a numerical string of a fixed length. This algorithm is most commonly used for securing and authenticating passwords. |
For more information on cryptography click here
For more information on ciphers click here
For more information on algorithms click here